Cybersecurity Best Practices: Protecting Your Digital Realm
1. Strong Passwords and Authentication:
- Use strong, unique passwords for each online account. Combine uppercase and lowercase letters, numbers, and symbols.
- Implement two-factor authentication (2FA) wherever possible, adding an extra layer of security.
- Consider using a reputable password manager to generate and store complex passwords securely.

2. Regular Software Updates:
- Keep your operating system, software, and applications up to date. Updates often contain critical security patches.
- Enable automatic updates to ensure you’re always protected against known vulnerabilities.

3. Phishing Awareness:
- Be vigilant about unsolicited emails and messages. Don’t click on links or download attachments from unknown sources.
- Verify the legitimacy of websites and email senders before providing sensitive information.
4. Firewalls and Antivirus Software:
- Install a trusted firewall and reputable antivirus software on all devices.
- Regularly update and run antivirus scans to identify and remove malware.

5. Data Encryption:
- Encrypt sensitive data both in transit (using HTTPS) and at rest (stored on devices or servers).
- Consider using a Virtual Private Network (VPN) for added privacy and security when accessing the internet.
6. Secure Wi-Fi Networks:
- Change default router passwords and use strong, unique Wi-Fi passwords.
- Enable network encryption (WPA3 or WPA2) and disable remote administration of your router.

7. Backup Your Data:
- Regularly back up important data to secure, offline storage. Ensure backups are reliable and tested for restoration.
- Consider using cloud-based backup services for added redundancy.
8. Employee Training:
- Educate employees about cybersecurity risks and best practices in a business setting.
- Establish clear guidelines for handling sensitive data and create a culture of security.
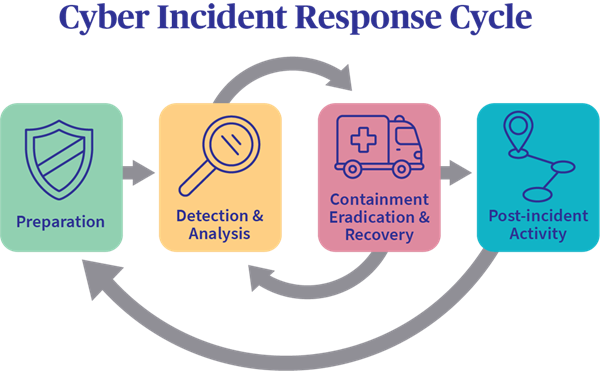
9. Incident Response Plan:
- Develop a detailed incident response plan that outlines steps to take in the event of a cybersecurity breach.
- Assign roles and responsibilities for managing and mitigating incidents.
10. Regular Security Audits: – Conduct routine security audits and vulnerability assessments to identify weaknesses in your digital infrastructure. – Address any vulnerabilities promptly to minimize risk.
Conclusion:
Cybersecurity best practices are the linchpin of a secure digital existence. By incorporating these principles into your online habits and business practices, you can significantly reduce your exposure to cyber threats. Remember that cybersecurity is not a one-time endeavor but an ongoing commitment to protect your digital realm. Stay informed about emerging threats, adapt your defenses accordingly, and foster a culture of security in your organization. In doing so, you’ll be well-equipped to navigate the digital world safely and confidently.
